Cybersecurity Primer - Part I
This is part 1 of a primer series on the Cybersecurity space for newbies, written by a generalist for generalists.
If this is your first time landing on my page, then you may have missed these recent posts:
Part 1
This first part of the series aims to provide an introduction to the Cybersecurity space. The series will then delve into key focus areas, including some deep dives on the companies I find most interesting within the sub sector.
Cybersecurity: the protection of internet-connected systems and networks from cyberattacks.
All companies connected to the internet need - and will always need - cybersecurity solutions.
Sizing the opportunity
Megatrends around cloud migration and digital transformation are expanding workloads, and creating new spending opportunities for cybersecurity. Software spend is expected to outpace all other IT spend to 2027, and within that, cybersecurity is expected to grow faster than all other sub-segments at 13% CAGR (source: Morgan Stanley).
There is a growing frequency of cyberattacks and increasing $ loss per attack. The cost of cyber crime was $8 trillion in 2023, and is expected to hit $10.5 trillion by next year (source: Cybersecurity Ventures). Cybersecurity is a top 10 global risk according to the World Economic Forum, and the average response time today to cyber breaches is 277 days (slow!!!). Unsurprisingly, enterprise IT budgets are burgeoning to deal with the threat.
Macro uncertainty during geopolitical events further the risks of cyber attacks. Take the example of the Russian hackers attacking the DNC network during the Trump v Clinton election of 2016!
Companies are only just beginning to realise the need to secure these new workloads, meaning there is a lag between cloud migration pace and cybersecurity penetration. This should then mean that even if cloud migration matures, cybersecurity adoption should continue.
Added to this is that as AI capabilities improve and become widely adopted by enterprises, cyber infrastructure becomes increasingly complex relative to prior architectures, thus requiring a broader cybersecurity footprint.
The global Cybersecurity TAM is worth $1.5+ trillion (source: McKinsey), which is 10x the size of the current penetration; today, overall cybersecurity spend is ~$150bn.
As a generalist, when first reading about the cybersecurity space I was taken aback by the level of jargon and acronyms - so below I attempt to boil it down to the need-to-know and it helped me to visualise using a castle (“network”) analogy.
The network layers
The primary goal of cybersecurity is to prevent unauthorised access into or between parts of a network.
There are 3 major parts of a company network:
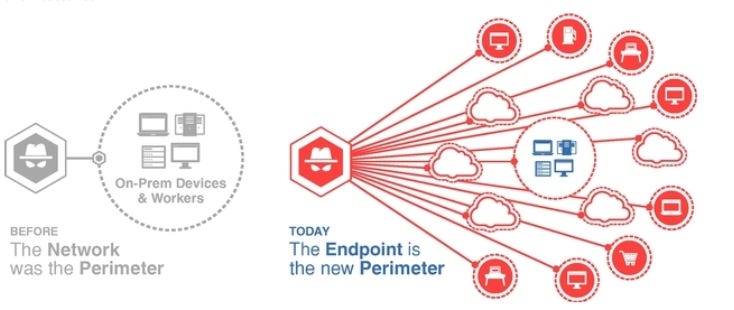
Traditionally, in-house network security solutions have assumed that the castle (internal core network) is a trusted zone that requires a moat (the perimeter) to be built and maintained to keep untrusted actors out, and only let permitted users in. Think VPN, WAN etc. This perimeter has typically been looked after by companies’ on-premise IT departments.
BUT - the hypergrowth of cloud infrastructure and SaaS services in a single company’s toolkit (think Microsoft 365 + Google Workspace + Dropbox + Slack + Zoom + Workday + Salesforce + Shopify + AWS + Azure + Google Cloud + XYZ…) mean that it is evermore cumbersome and complicated for the company to internally manage a solid perimeter. As data travels to and from all these SaaS services, the opportunity window widens for malicious activity and threats.
Who are these attackers?
Governments (cyberwarfare)
Terrorists (cyberterrorism)
Industrial spies
Hackers
Business competitors
Unhappy insiders
How do they attack?
Some common attacks include,but aren’t limited to:
Malware: hidden software (eg. viruses, trojan horses, spyware, ransomware) planted on the company system to capture sensitive data or gain access.
Malvertising: online ads where clicks lead to malware installation.
Social engineering: deceiving staff into divulging sensitive information or system access. Examples are phishing emails disguised as legitimate messages that attempt to lure employees onto a fake website in order to capture user credentials.
Distributed Denial of Service (DDoS) attack: a coordinated attack against a company’s servers to disrupt normal traffic and overwhelm it by flooding it with bogus requests.
Brute Force Attack: attempts to force into an account by guessing as many possible combinations of credentials as possible.
Spyware: malware that allows a user to spy on the user, such as a keyboard logger or camera or mic capture.
Wifi spoofing: a fake wifi network to fool users into connecting to it, to eavesdrop on their network traffic.
Account hijacking: using stolen account credentials to conduct malicious or unauthorized activity.
Companies need to protect ALL traffic between the core internal trusted network and SaaS services to ensure no data is leaking out, and no bad activity is coming in - i.e. NO GAPS in the network security.
Zero Trust
Under the traditional on-premise IT approach, there is a trusted zone with a firewall fence separating this “safe” core from anything beyond the perimeter. But a major downside of this is that once a threat gets inside the perimeter, it can move all over the trusted network. Once inside the castle, an intruder can go to any room.
This has led to a new approach - Zero Trust. This is a new paradigm that replaces the trusted perimeter with zero trust (regardless of whether an entity is inside or outside the castle) until an identity is established.
Zero Trust essentially means no perimeter, and hence, no edge gateways needed. What was edge compute becomes just another server or service. Every server becomes just another endpoint - so your network essentially becomes endpoint-to-endpoint.
The way I think of it is likening legacy cybersecurity players like McAfee to airport security; you would get stopped for carrying liquids or knives at the TSA checkpoint, but beyond that you could potentially carry things undetected - so all you have to figure out is how to fool the system once. Zero trust is like a casino where you’re checked when you come in but then you’re also always being watched on your activity to detect is something nefarious is happening.
SecaaS
Security-as-a-Service (SECaaS): A SaaS company providing cybersecurity services to firms.
Types of SecaaS:
Identity tracking: tracks users and their access rights
Monitoring & detection: services for monitoring systems or detecting abnormal or threatening behaviours on your network
Protection: take action to protect your network
Response: systems to automate response handling or help react to an incident
A good SECaaS company:
Disrupts the status quo of traditional network security - eg. adopts Zero Trust
Is cloud native so it can scale and seamlessly reach all endpoint devices
Is platform based - so the customer company can aggregate their security efforts so as to integrate easily with other services it relies on
Is a platform play, innovating into adjacent product lines and markets. There must be new products being developed (organically or acquired) that leverage the existing platform. The rate of customer requirement change is vast because the top cybersecurity risks are constantly changing. This also fuels new hypergrowth after growth of the initial core product matures.
The HACK Index is an ETF giving acess to listed cybersecurity companies, and it has underperformed the S&P500. This is fundamentally because cybersecurity evolves rapidly in response to rapidly evolving threat vectors, leaving few vendors with persistent, durable LT growth.
There are broadly 5 key categories of vendors competing in the cybersecurity space:
Legacy vendors (eg. winners from previous tech horizons)
Hyperscalers (eg. AWS)
Platform consolidators (eg. Microsoft, Palo Alto Networks)
Private players backed by VC
Best of breed pure-play point solutions
Hyperscalers and platform consolidators have consistently attempted to become the domiant, de-facto cybersecurity player. A player like AWS has a huge distribution advantage which can tip it into favour for many enterprise customers (especially smaller ones). However, these players have historically faced challenges:
It is trickier to provide cybersecurity solutions beyond the hyperscaler’s own cloud network. Enterprises typically operate in multi cloud environments and trust independent solution providers to deliver consistent results across all their cloud networks.
Adding cybersecurity as a side gig can mean an inferior solution versus pure play, specialist cybersecurity players. Yes, hyperscalers can offer cybersecurity solutions with no/ low integration costs and have been “good enough” in the past; but with the threats as complex as they are now, good enough isn’t enough. Case in point, Microsoft has had a series of concerning breaches - see here. A cheaper, “good enough” bullet proof vest is worthless if it doesn’t fully protect from a bullet. Point being that companies, particularly large ones, are likely to shift towards quality (from specialist players) over price.
The largest pure-play competitors are as follows:
With this post aiming to be an introductory overview for the space, I will deep dive on who does what, and some of these companies in my next few posts.
Thanks for reading! As always please let me know your thoughts via the buttons below.